Security CONSULTING
It is a detailed objective examination of the security related risks from internal and external threats, exploitable deficiencies, and non-conformity with security standards of an entity in order to appropriately provide recommended mitigations to the unwanted negative consequences to people property, information assets or reputation. Our aim is to increase profitability and decrease liability.
Training & INSTRUCTION
Training is the cornerstone of preparation. It is fundamental in mitigating any potential liability or loss. It can help you prevent unwanted events, prepare for them if they do happen, and improve your resiliency for once they do. Classes include:
- Active Shooter
- School Safety
- Facility Hardening
- First-Aid / CPR / AED
- Post Orders
Physical
Security
Physical Security involves systems that relate to electronic or mechanical means that enable various layers of deterrence, detection, delaying or denying someone or something, as well defending, protecting, alerting us to and identifying someone or something. This includes:
- CCTV Cameras
- Sensors
- Alarms
- Barriers
- Locks
- Fences
TECHNICAL SURVEILLANCE COUNTER MEASURES (TSCM)
Electronic counter-surveillance techniques to detect, neutralize, and exploit technical surveillance technologies and hazards that permit the unauthorized access to or removal of information. The goal is to protect and safeguard sensitive information and confidential communications from potential eavesdropping threats and attacks.
SECURITY
CONSULTING
At the core, Security Consulting is an objective review that identifies and quantifies deficiencies, as well as propose viable and cost effective solutions in order to mitigate risks.
The processes we apply can involve one or more of the below systematic approaches and rely on established authoritative standards and guidelines in order to advise you.
If you are in need of an objective analysis to comply with established security policies, insurance requirements, requirements due to contract terms, or you are forward thinking and want to mitigate any liabilities you may be facing,
our expertise is available and we are here to help you.

SECURITY SURVEY / AUDIT
A comprehensive review of policies, procedures and facts in order to identify problems and potential liabilities, as well as confirm actualities or expectations such as contractual obligations and requirements. It is a detailed report that:
- Has a Rational and Orderly approach
- Provides management vital information on which to base sound decisions
- Identifies areas of greater (or lesser) security need
- Identifies areas of weakness and strength

RISK ANALYSIS
A management tool in which we:
- Identify the assets in need of protection,
- Identify the risks that may affect the assets,
- Determine the probability of the identified risks occurring,
- Determine the impact or effect on the organization in dollar values when possible, if a given loss does occur.
We then develop risk mitigation options that include assessing the feasibility of implementation, as well as a cost / benefit analysis.
THREAT ASSESSMENT &
management STRATEGY
The use of a fact based method of assessment and investigation that focuses on an individuals patterns of thinking and behavior to determine whether, and to what extent, he or she is moving toward an attack on an identifiable target.
If warranted, this culminates in a plan of direct or indirect interventions with the subject that, based on current information regarding level of threat posed, is designed to defuse the risk in a given situation at a particular point in time.

TRAINING
Training is the bedrock of preparation and key to performance at a high level. Our years of experience in the security industry, repeated requirements of our own continuing education, as well as dedication to our field of expertise,
has given us a unique capability to now teach these skills.
The following courses are available for scheduling:
SCHOOL SAFETY & SOFT TARGET HARDENING
Covering a wide scope ranging from Behavioral Threat Assessment, Visual Weapons Screening, Bomb Threat Management, Bus Safety Awareness, to Severe Weather and Natural Disaster Planning.
WORKPLACE VIOLENCE PREVENTION
Assessing the extent of violence in the workplace, the hazards in different settings and developing workplace violence prevention plans for individual worksites.
ACTIVE SHOOTER – WHAT TO DO AND WHAT TO EXPECT
Because active shooter situations are often over before law enforcement arrives on the scene, individuals must be prepared, both mentally and physically, to deal with an active shooter situation.
POST ORDERS & HOW THEY SHOULD BE WRITTEN
The basic building block of a quality professional security program. It is a detailed written set of references and instructions that lays out all there is to know about a specific post or specific assignment. Without it, chaos will rule the day, lackluster performance will be the norm, and guaranteed failure of all affected.
EMERGENCY RESPONSE PLAN & PROCEDURES
Need to get an Emergency Response Plan in place? Does your organization have plans in place if there should ever arise the need for commonly occurring emergencies or natural disasters? Such events WILL happen, and mitigating the liability of such events is paramount to overcoming them.
FACILITY EMERGENCY RESPONSE TEAMS
Need to get an Emergency Response Team up and running, trained and ready to respond? Are your employees and your staff able to respond to commonly occurring emergencies and natural disasters? Can they be the difference when time and action matters?
FIRST-AID
CPR / AED
EMERGENCY RESPONSE TRAINING
Stop the Bleed, First-Aid, CPR & AED training. When help is on the way but you are suddenly forced to be the first responder. Everyone should know these basic steps to help save lives until professional help arrives on scene. Instruction will include:
- What is First Aid?
- Good Samaritan Laws
- Scene and Victim Assessment
- First Aid Kits
- PPE
- Physical Injuries
- Bleeding emergencies & use of Tourniquet
- Burn Injuries
- Strains, Sprains, and Fractures
- Breathing Emergencies
- CPR Certification
- AED Certification
*Coming Soon:
Georgia Board of Private Detectives and Security Agencies
24HR BASIC SECURITY OFFICER COURSE
Course will cover: All State mandated topic as outlined in Rule 509-3.02, including:
- Role of Private Security
- Legal Aspects
- Patrol and Observation
- Incident Response
- Security Resources
- Customer Service Issues
- First Aid Overview
*Coming Soon:
Georgia Board of Private Detectives and Security Agencies
16HR BASIC ARMED OFFICER COURSE
Course will cover: All State mandated topics as outline in Rule 509-3.03, including:
- Use of deadly force
- Liability Issues
- Ballistics
- Handgun Types
- Range Qualification
PHYSICAL SECURITY
Physical Security is the protection of personnel, property, and information from physical actions and events that could cause serious loss or damage to an enterprise, agency or institution. This includes protection from fire, flood,
natural disasters, burglary, theft, vandalism or terrorism. The goal is a multi-layered approach to Deter, Detect, Delay Deny, or Defend.
E.S.P.I. can help you design a proper physical security system from the ground up or evaluate your existing one to ensure optimal performance, safety and security.
DETER
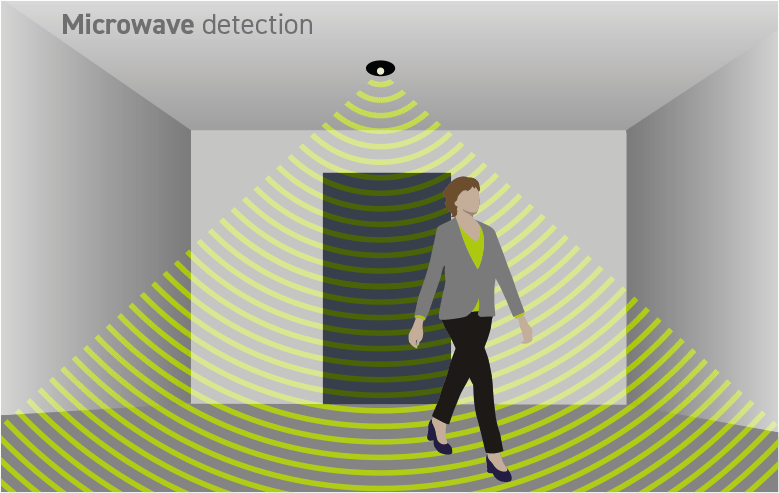
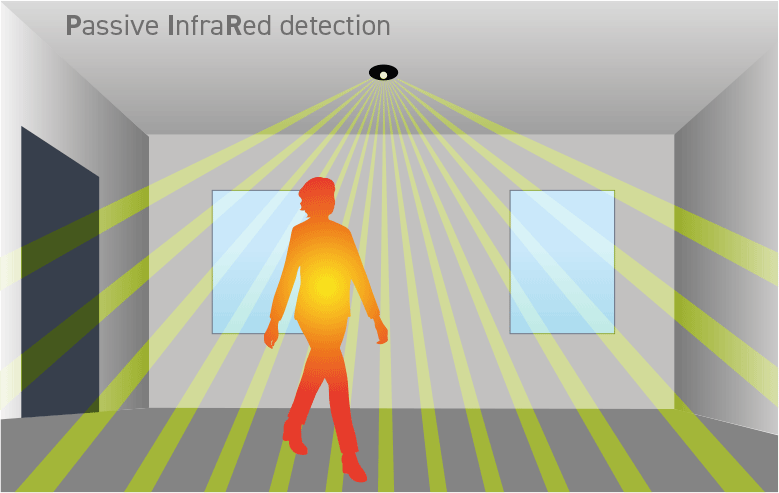
Deterrence is the first line of defense. It involves creating a visible and effective security presence that discourages potential threats from even attempting to breach the perimeter. This can include physical barriers, such as fences and gates, as well as security cameras, alarms, active security personnel and signage. The goal is to make it clear to potential attackers that the facility or system is well-protected and that any attempt to breach it will be met with resistance.
DETECT
Detection is the process of identifying potential threats as early as possible. This can involve a range of technologies, such as motion sensors, video analytics, and intrusion detection systems. The goal is to detect threats before they have a chance to breach the perimeter and enter the facility or system.
DELAY
Delay is the act of slowing down a threat once it has breached the perimeter. This can involve physical obstacles, such as bollards and barriers, as well as security personnel who are trained to respond quickly and effectively to a breach. The goal is to buy time for security personnel to respond and neutralize the threat before it can cause any damage.
DENY
Denial is the act of preventing a threat from gaining access to the facility or system. This can involve physical barriers, such as fences and gates, as well as access control systems, such as biometric scanners and keycard readers. The goal is to make it as difficult as possible for a threat to breach the perimeter and gain access to the facility or system.
DEFEND
Defending is the act of neutralizing a threat once it has breached the perimeter. This can involve a range of tactics, from physical force to cybersecurity measures, such as firewalls and intrusion prevention systems. The goal is to stop the threat and prevent it from causing any further damage.
Achieving this goal is accomplished through the use of numerous tools such as:





- Cameras & Video Surveillance
- Sensors & Detection Devices
- Access Controls
- Alarms
- Locks
- Control Centers
- Barriers
- Fences & Gates
- Exterior Lighting
- Specialty Windows
- CPTED (Crime Prevention Through Environmental Design)
- Security Personnel
- Visitor Management
- Storage Containers & Vaults
- Safe Rooms
- Policies
- Procedures
TSCM
TSCM is an acronym that refers means Technical Surveillance Counter Measures. It is a very specific area of specialization within the security industry that detects, locates, and neutralizes bugging devices and identifies technical
security vulnerabilities.
The goal is to protect and safeguard sensitive information and confidential communications from potential eavesdropping threats by performing visual inspections and environmental scans.
If you believe that your private or business conversations are being intercepted, if proprietary or confidential information is being leaked, or you are suspicious of the existence of a listening device and believe you are the victim of electronic surveillance, please contact us today.
We can assist in the electronic surveillance management:
- In areas of Residential and Domestic Issues
- In areas of Corporate Counter Espionage
- In areas of Counter Surveillance
And detect electronic surveillance through:
- Boardroom Sweeps
- Conference Room Sweeps
- Executive Home Office Sweeps
- Hotel & Off-site Meeting Sweeps
- Vehicle Sweeps
- Executive Aircraft Analysis & Sweep
- Ongoing monitoring of meetings and / or conferences
Please Note:
If you believe that your private or business conversations are being intercepted, please contact us from a different location other than the location you believe to be compromised, as well as from a communication device not connected to you.
For example, if you believe there is a bug somewhere in your office, DO NOT contact us from your office space, using the office phone, or from your office computer.

Identifying Devices
Specialized Equipment, such as spectrum analyzers and radio frequency detectors, non-linear junction detectors, ultraviolet inspection lights, thermal cameras, video borescopes and other tools are used to identify and locate audio and video devices.


Eavesdropping Devices
These technologically advanced devices are hard to find and are increasingly becoming smaller, more sophisticated, and more covert. Even worse, they are easily purchased and publicly available these day on various websites and stores. However, only a trained professional who has developed the necessary technical skill and obtained the required experience to properly use specialized equipment can locate these devices for you.

Defensive Tools
Audio security tools such as acoustic noise generators, pictured above, can help protect proprietary or sensitive conversations against threats from perimeter contact microphones and reflected laser listening devices by injecting tuned masking noise (White Noise).
CONTACT US
Please tell us a little about yourself and the reason you are contacting us. We will respond as soon as possible after having received your request.
We appreciate your patience.
info@espi-llc.com
Phone: 770-676-7906


